Gateway API Canary Deployments
This guide shows you how to use Gateway API and Flagger to automate canary deployments and A/B testing.
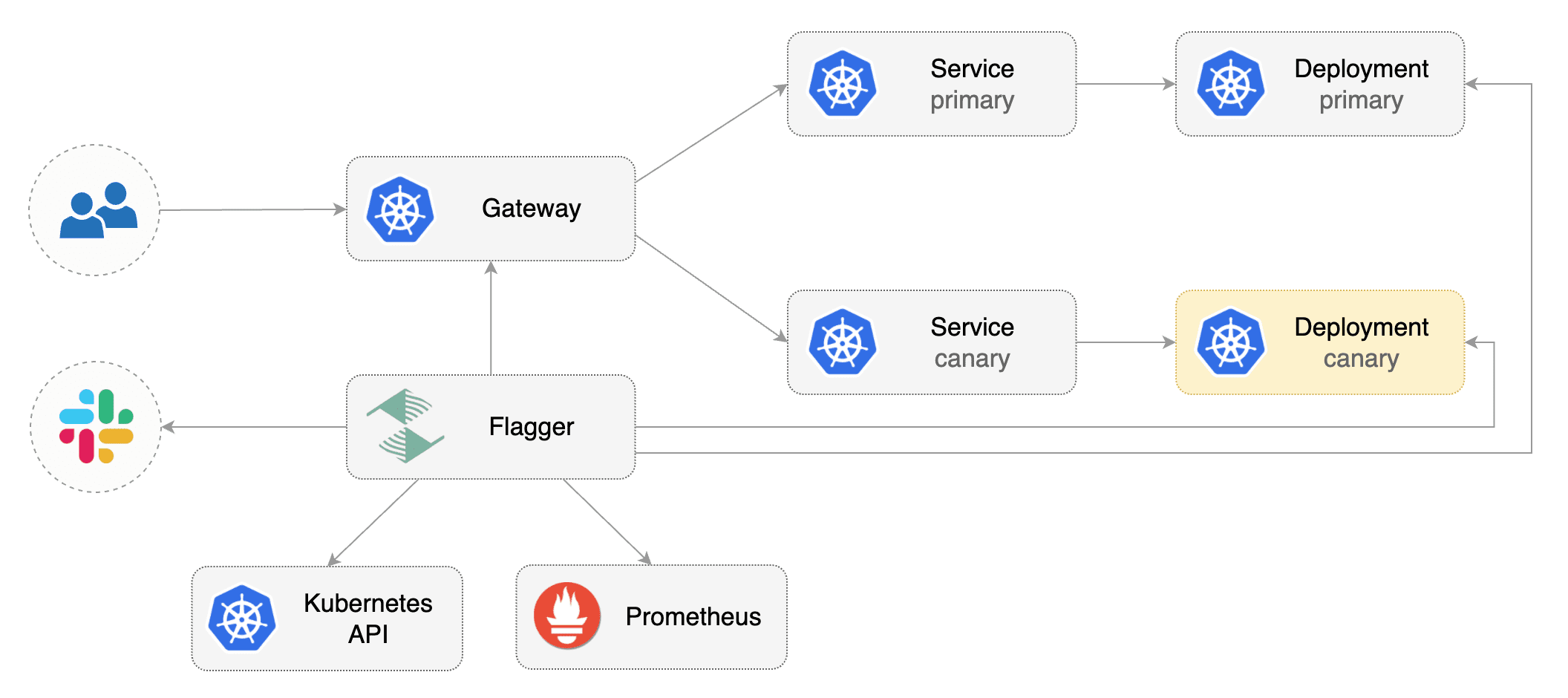
Prerequisites
Flagger requires an ingress controller or service mesh that implements the Gateway API HTTPRoute (v1 or v1beta1).
We'll be using Istio for the sake of this tutorial, but you can use any other implementation.
Install the Gateway API CRDs:
Install Istio:
Install Flagger in the flagger-system namespace:
Create a namespace for the Gateway:
Create a Gateway that configures load balancing, traffic ACL, etc:
Bootstrap
Flagger takes a Kubernetes deployment and optionally a horizontal pod autoscaler (HPA), then creates a series of objects (Kubernetes deployments, ClusterIP services, HTTPRoutes for the Gateway). These objects expose the application inside the mesh and drive the canary analysis and promotion.
Create a test namespace:
Create a deployment and a horizontal pod autoscaler:
Deploy the load testing service to generate traffic during the canary analysis:
Create metric templates targeting the Prometheus server in the flagger-system namespace. The PromQL queries below are meant for Envoy, but you can change it to your ingress/mesh provider accordingly.
Save the above resource as metric-templates.yaml and then apply it:
Create a Canary custom resource (replace "www.example.com" with your own domain):
Save the above resource as podinfo-canary.yaml and then apply it:
When the canary analysis starts, Flagger will call the pre-rollout webhooks before routing traffic to the canary. The canary analysis will run for five minutes while validating the HTTP metrics and rollout hooks every minute.
After a couple of seconds Flagger will create the canary objects:
Expose the app outside the cluster
Find the external address of Istio's load balancer:
Configure your DNS server with a CNAME record (AWS) or A record (GKE/AKS/DOKS) and point a domain e.g. www.example.com to the LB address.
Now you can access the podinfo UI using your domain address.
Note that you should be using HTTPS when exposing production workloads on internet. If you're using a local cluster you can port forward to the Envoy LoadBalancer service:
Now you can access podinfo via curl -H "Host: www.example.com" localhost:8080.
Automated canary promotion
With the application bootstrapped, Flagger will continuously monitor the deployment for changes. When a new revision is detected, Flagger will start a canary analysis and gradually shift traffic to the new version.
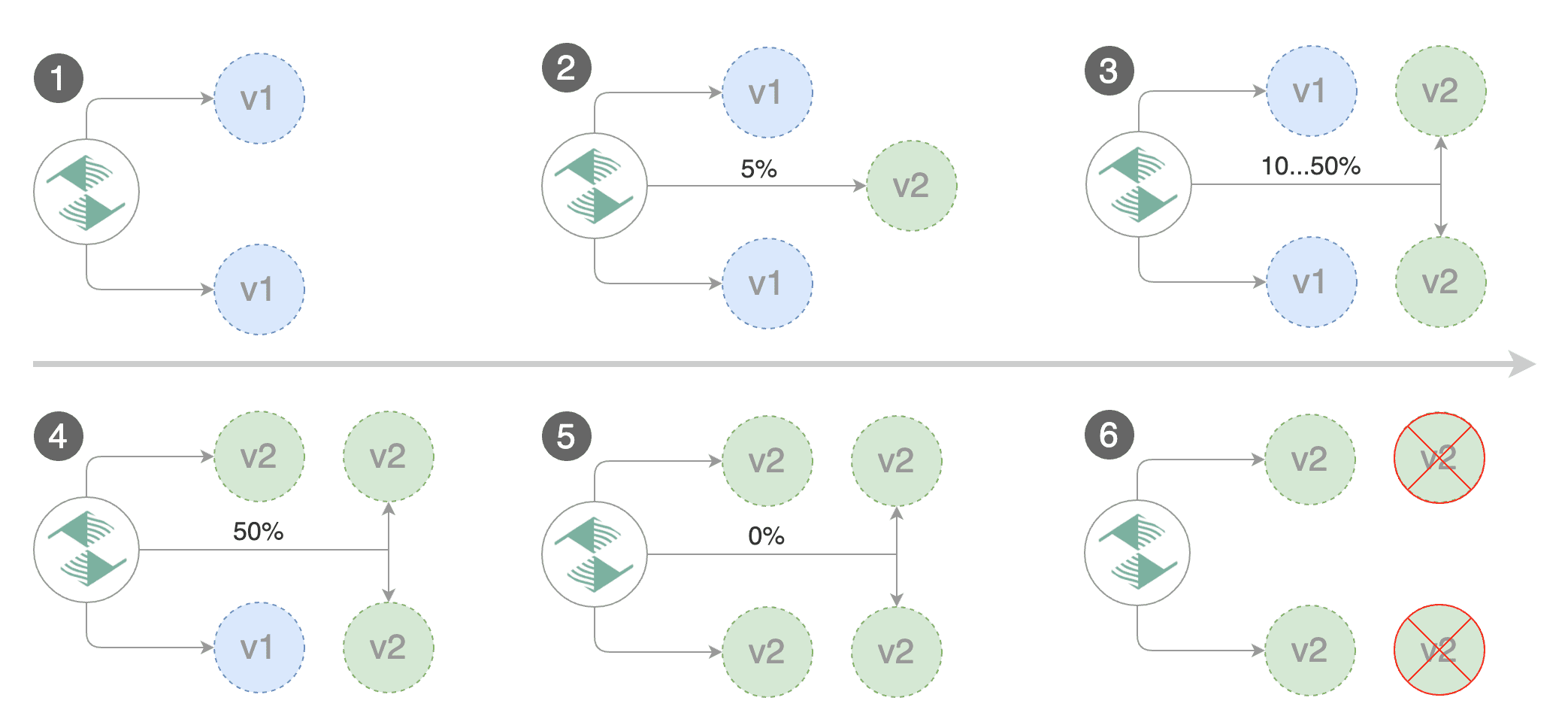
Trigger a canary deployment by updating the container image:
Flagger detects that the deployment revision changed and starts a new rollout:
Note that if you apply new changes to the deployment during the canary analysis, Flagger will restart the analysis.
A canary deployment is triggered by changes in any of the following objects:
Deployment PodSpec (container image, command, ports, env, resources, etc)
ConfigMaps mounted as volumes or mapped to environment variables
Secrets mounted as volumes or mapped to environment variables
You can monitor how Flagger progressively changes the weights of the HTTPRoute object that is attached to the Gateway with:
You can monitor all canaries with:
Automated rollback
During the canary analysis you can generate HTTP 500 errors and high latency to test if Flagger pauses the rollout.
Trigger another canary deployment:
Exec into the load tester pod with:
Generate HTTP 500 errors:
Generate latency:
When the number of failed checks reaches the canary analysis threshold, the traffic is routed back to the primary, the canary is scaled to zero and the rollout is marked as failed.
A/B Testing
Besides weighted routing, Flagger can be configured to route traffic to the canary based on HTTP match conditions. In an A/B testing scenario, you'll be using HTTP headers and cookies to target a certain segment of your users.
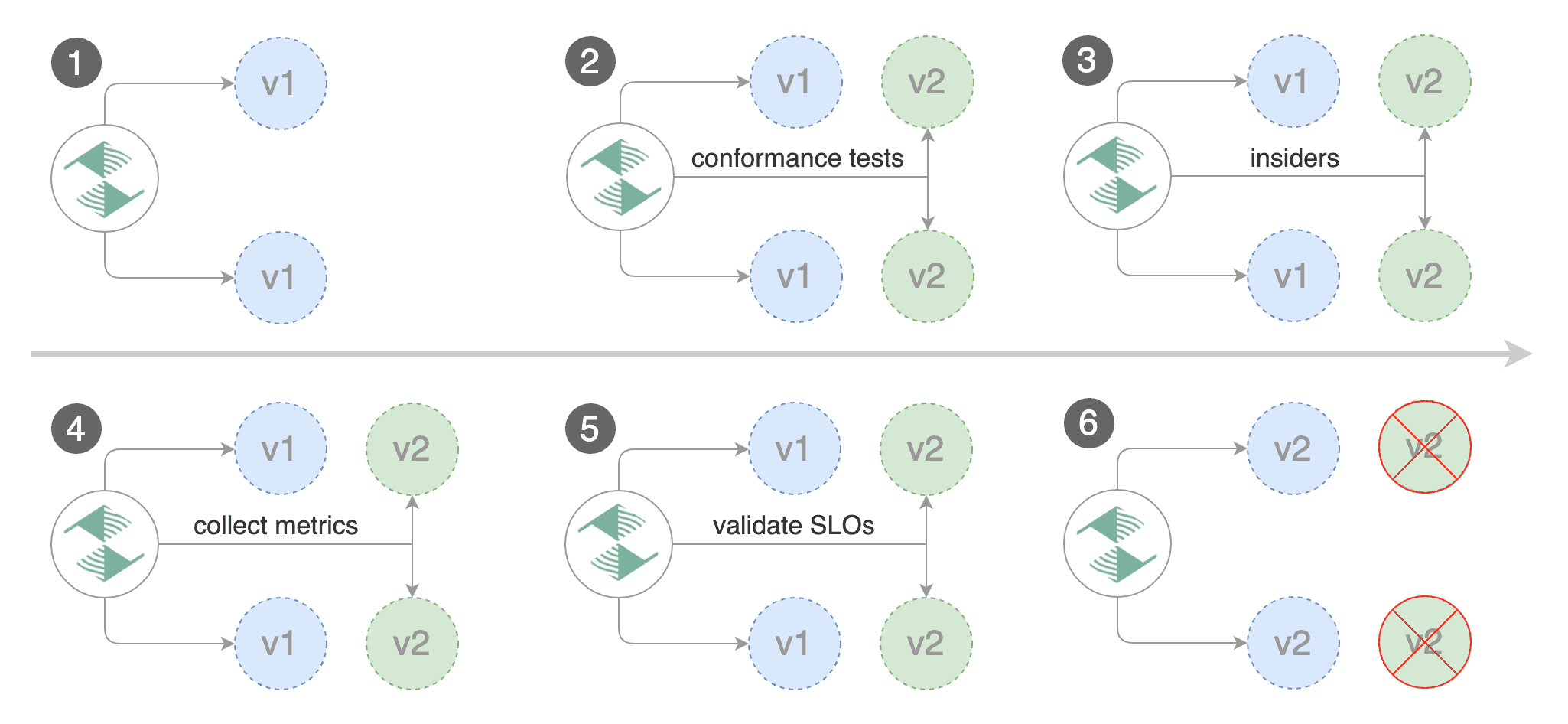
Create a canary custom resource (replace "www.example.com" with your own domain):
The above configuration will run an analysis for ten minutes targeting those users that have an insider cookie or are using Firefox as a browser.
Save the above resource as podinfo-ab-canary.yaml and then apply it:
Trigger a canary deployment by updating the container image:
Flagger detects that the deployment revision changed and starts a new rollout:
Session Affinity
While Flagger can perform weighted routing and A/B testing individually, with Gateway API it can combine the two leading to a Canary release with session affinity. For more information you can read the deployment strategies docs.
Note: Session Affinity requires a Gateway API implementation that supports the
ResponseHeaderModifierAPI.
Create a canary custom resource (replace www.example.com with your own domain):
Save the above resource as podinfo-canary-session-affinity.yaml and then apply it:
Trigger a canary deployment by updating the container image:
You can load www.example.com in your browser and refresh it until you see the requests being served by podinfo:6.0.1. All subsequent requests after that will be served by podinfo:6.0.1 and not podinfo:6.0.0 because of the session affinity configured by Flagger in the HTTPRoute object.
To configure stickiness for the Primary deployment to ensure fair weighted traffic routing, please checkout the deployment strategies docs.
Traffic mirroring
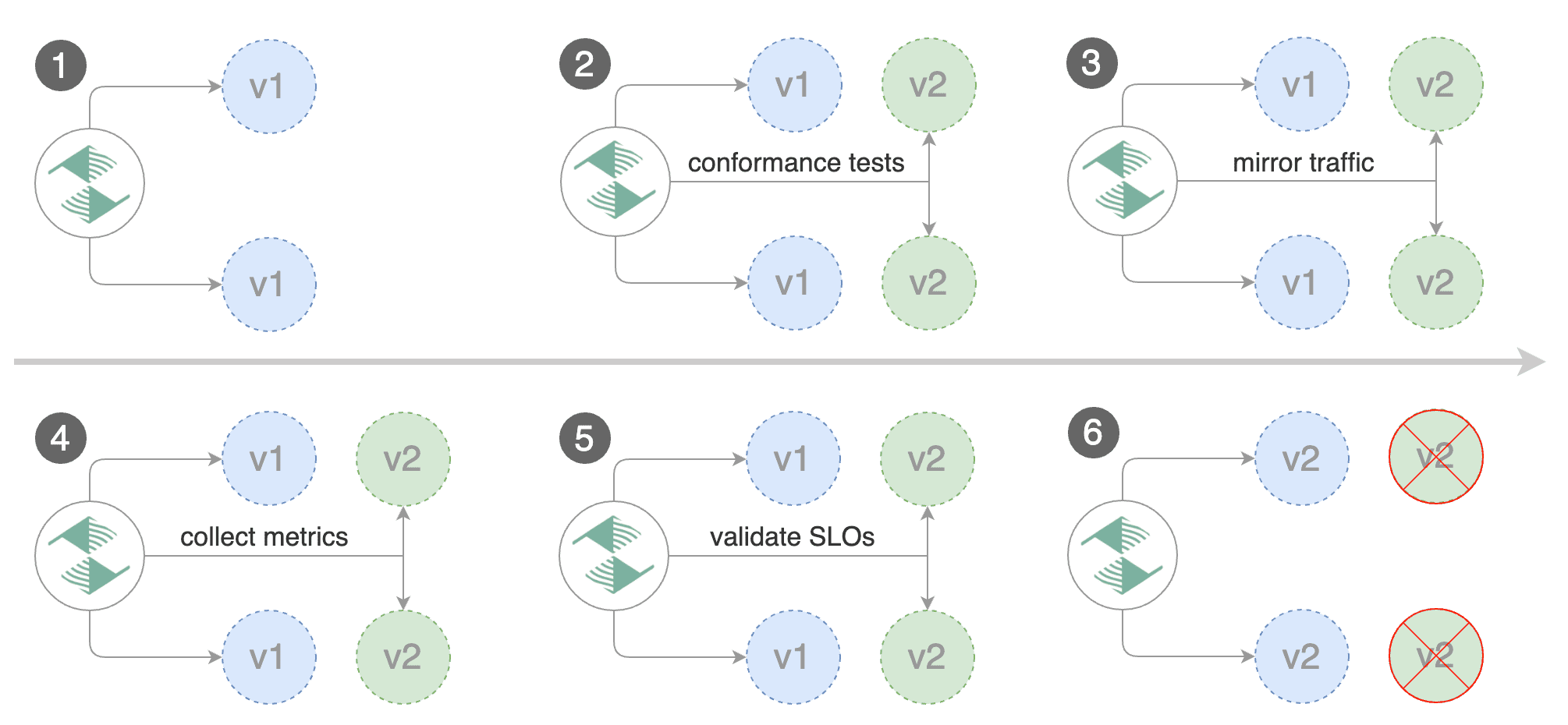
For applications that perform read operations, Flagger can be configured to do B/G tests with traffic mirroring.
Note: Traffic mirroring requires a Gateway API implementation that supports the
RequestMirrorfilter.
You can enable mirroring by replacing stepWeight with iterations and by setting analysis.mirror to true:
Gateway API traffic mirroring will copy each incoming request, sending one request to the primary and one to the canary service. The response from the primary is sent back to the user and the response from the canary is discarded.
Metrics are collected on both requests so that the deployment will only proceed if the canary metrics are within the threshold values.
The above procedures can be extended with custom metrics checks, webhooks, manual promotion approval and Slack or MS Teams notifications.
Customising the HTTPRoute
Besides the hosts and gatewayRefs fields, you can customize the generated HTTPRoute with various options exposed under the spec.service field of the Canary.
Header Manipulation
You can configure request and response header manipulation using the spec.service.headers field of the Canary.
Note: Header manipulation requires a Gateway API implementation that supports the
RequestHeaderModifierandResponseHeaderModifierfilters.
Example configuration:
URL Rewriting
You can configure URL rewriting using the spec.service.rewrite field of the Canary to modify the path or hostname of requests.
Note: URL rewriting requires a Gateway API implementation that supports the
URLRewritefilter.
Example configuration:
The type field determines how the URI rewriting is performed:
ReplaceFullPath: Replaces the entire request path with the specified
urivalueReplacePrefixMatch: Replaces only the prefix portion of the path that was matched
Example with prefix replacement:
When using ReplacePrefixMatch, if a request comes to /old/path, and the HTTPRoute matches the prefix /old, the request will be rewritten to /api/v2/path.
CORS Policy
The cross-origin resource sharing policy can be configured the spec.service.corsPolicy field of the Canary.
Note: Cross-origin resource sharing requires a Gateway API implementation that supports the
CORSfilter.
Example configuration:
Last updated
Was this helpful?